In early October 2025, DraftKings alerted some of its users that their accounts were compromised in what appears to be a credential stuffing attack. BleepingComputer While the scale was ultimately small (fewer than 30 customers affected, per a later update) BleepingComputer, the incident is an instructive case study for anyone running an online platform, app, or service. It underlines how even large brands aren’t immune—and how credential reuse across sites remains a potent vulnerability.
Let’s unpack what happened, why it matters to tech and business audiences, and how to build stronger defenses against credential-based attacks.
What Happened: The DraftKings Attack in a Nutshell
Here’s a summary of the incident:
- DraftKings discovered that attackers had gained access to some user accounts using login credentials stolen from external (non-DraftKings) sources. In other words, users had reused usernames/passwords that had already leaked elsewhere. BleepingComputer
- The attackers leveraged automated tools to test credential lists en masse (a standard technique in credential stuffing). BleepingComputer+1
- Once inside, they were able to view non-sensitive personal data: name, address, DOB, phone, email, some transaction history, account balance, profile photo, and the last four of payment cards. But according to DraftKings, they did not access sensitive items like full financial account numbers or government ID numbers. BleepingComputer
- DraftKings forced affected customers to reset passwords and required enabling multifactor authentication (MFA) for some accounts. BleepingComputer
- DraftKings later clarified that fewer than 30 customers were impacted and said there was “no evidence that … DraftKings’ computer systems or networks were breached.” BleepingComputer
- Past history: In 2022, a similar credential stuffing campaign against DraftKings resulted in ~$300,000 stolen; the company refunded affected customers then. BleepingComputer
While the damage in this latest incident was limited, the methodology is far from novel—and it’s only getting more efficient and dangerous.
Why This Matters to the Tech & Business Community
- Credential reuse is a systemic weak point.
Many breaches or leaks from one service end up weaponized against your users at your platform. Even if your system is secure, the fact that users use the same password elsewhere gives attackers a foothold. - Automation makes this threat scalable.
Tools for credential stuffing are easily available, lowering the barrier for attackers to test thousands or millions of credential pairs rapidly. - Reputation & customer trust are on the line.
Even if the direct impact is small, users may lose faith in your platform’s security. The brand blowback and PR cost are nontrivial. - Defense is not optional—it’s a competitive differentiator.
Showing users you take proactive steps (MFA, anomaly detection, login hardening) can be a selling point in a crowded market. - The downstream costs can escalate.
Credential stuffing is often a stepping stone to further attacks—account takeover, financial fraud, identity theft, or phishing campaigns using accessed data.
Actionable Tips to Harden Against Credential Stuffing
Here’s what you can do now to reduce your exposure:
| Area | Recommendation | Why It Helps |
|---|---|---|
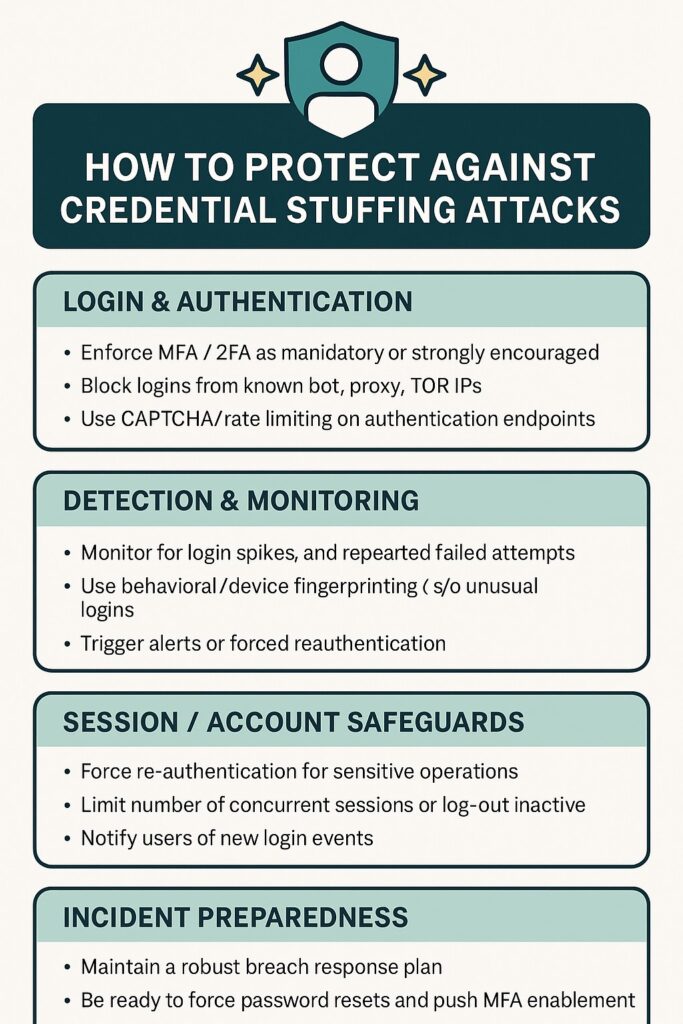
| Login & Authentication | – Enforce MFA / 2FA as mandatory (or at least strongly encouraged) – Block logins from known bot / proxy / TOR IPs – Use CAPTCHA / rate limiting on authentication endpoints | Adds friction to automated attacks and makes brute forcing much harder |
| Detection & Monitoring | – Monitor for login spikes, repeated failed login attempts, velocity anomalies – Use behavioral / device fingerprinting to detect unusual logins – Trigger alerts or forced reauthentication on suspicious sessions | Early detection limits damage |
| Credential Hygiene | – Encourage (or force) users to use unique, strong passwords – Offer password managers or suggest their use – Check (without storing) user passwords against public leak databases (e.g. “Have I Been Pwned”) | Reduces the chance that a user’s credentials are reused from a compromised service |
| Session / Account Safeguards | – Force re-authentication for sensitive operations (e.g. changing payment info) – Limit the number of concurrent sessions or log out inactive sessions – Notify users of new login events (with location, device info) | Limits an attacker’s ability to escalate once they gain access |
| Incident Preparedness | – Maintain a robust breach response plan – Be ready to force password resets and push MFA enablement – Provide clear communication to users – Audit what data your system collects and stores (minimize what’s available in case of breach) | When prevention fails, speed and clarity in response reduce reputational harm |
A Few Caveats & Considerations
- User convenience vs. security tradeoff: Overzealous protection (too many friction points) can frustrate users. Balance usability with defense.
- False positives: Anomaly detection systems may flag legitimate users, so have fallback verification or human review channels.
- Data privacy & compliance: Always be careful about how you store and use user data (logs, device IDs). Ensure your monitoring doesn’t inadvertently violate user privacy or regulations.
- Zero risk is a myth: Even big, well-funded platforms get breached. The goal is risk reduction and response readiness, not perfect invincibility.
Final Word
The DraftKings incident is a reminder that credential stuffing remains a potent threat — and that even large brands must stay vigilant. For startups, SaaS platforms, and tech entrepreneurs, this should serve as a wake-up call: don’t wait until after a breach to upgrade your defenses.
If you’re building or managing a product or service with user authentication, take this as a checklist moment. Ask: “If today an attacker had a trove of username/password pairs, how long would it take to compromise my user base?” If your answer isn’t “not even possible,” then there’s work to do.




