Over the last few weeks we have received reports from folks asking about an email they have received. When we started to review the various emails we found that they were being sent a very similar ransomware. Of course they were a bit embarrassed and didn’t want to ask for help. That’s exactly what the perpetrators are hoping for.
It starts out with an email below. They start off by showing you that they have your password which alarms you right away. They then begin to explain that they have hacked your computer and have access to your webcam and have screen captured websites you have visited. Where it gets sketchy is that they state they have recordings of the porn websites you visited and have recordings of you while on these sites.
The next piece of the email is the ransom. They give you 2 options. The first involves you sending them a specific dollars amount of bitcoin. We have seen this number vary from email to email. Option 2 is you do nothing and they send this video file to various people in your contacts list. An example of this email is below.
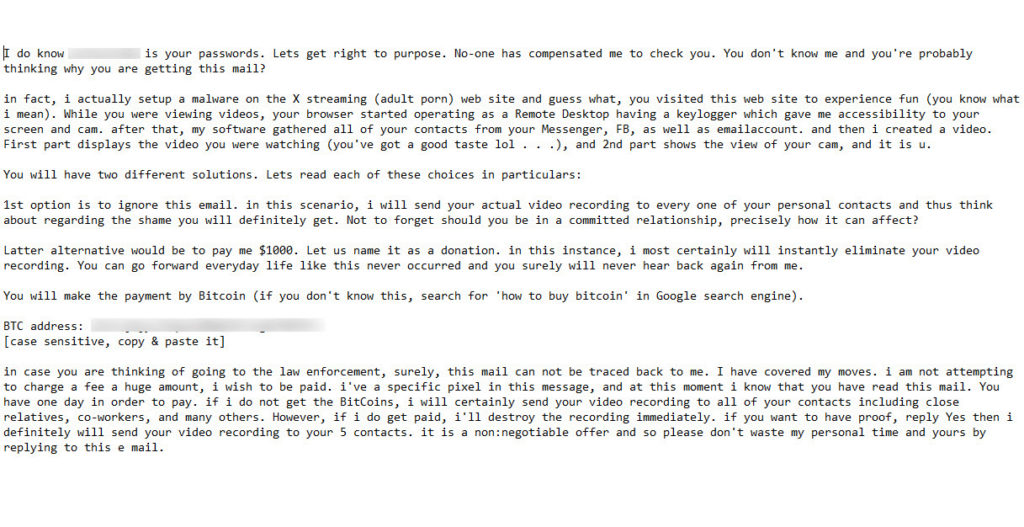
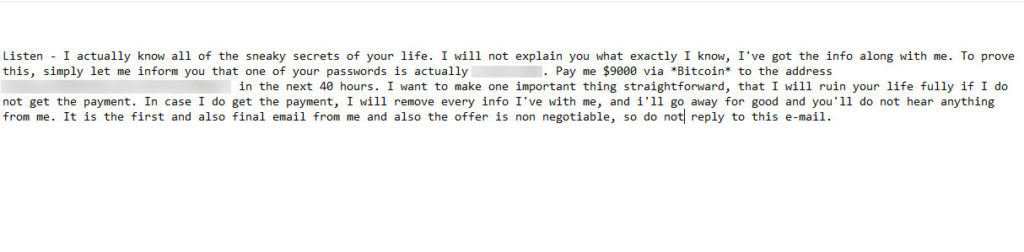
Here is another version. Not as descriptive as the example above but the hooks are the same. We have an embarrassing video of you and will share it with your contacts unless you pay us money.
While there are examples of Porn malware used in the past to hack individuals like the Adult Player App. Carl Leonard, principal security analyst at Forcepoint, said cyber-extortion is a prevalent tactic today. While it largely takes the form of ransomware, he said data exposure threats were growing in popularity.
“Cyber-blackmailing continue to prove as an effective tactic for cyber criminals to cash out on their malicious operations,” he said. “In this case, it appears that a threat actor group originally involved in adult dating scams have expanded their operations to cyber-extortion campaigns as a result of this trend.”
But Mr Leonard said the scale of this campaign suggested the scammers were bluffing about having compromising information.
“While no threat can be completely discounted, the compromise of personal information for this many individuals would constitute a significant breach of one or more websites, yet no activity of this nature has been reported or identified in recent weeks,” he said.
“Furthermore, if the actors did indeed possess personal details of the recipients, it seems likely they would have included elements [such as name, address or date of birth] in more targeted threat emails in order to increase their credibility. This led us to believe that these are simply fake extortion emails. We ended up calling it ‘faketortion’.”
In some cases we did find that the passwords shown in the email were of the user. Those might have been part of other hack jobs and sold on the Dark Web. If your password is one that you use for any site make sure to change that and no longer use that. Try using a tool like Lastpass or OnePassword to help you manage and use more cryptic passwords on all of your sites.




